WannaCrypt ransomware worm, aka WanaCrypt, Wanna Crypt0r or Wcry has crippled Windows systems in at least 74 countries, from government departments to local butchers. At the moment it appears there are up to 16 NHS health trusts taken out by the malware, FedEx in the US, Telefonica and Santander in Spain, Scottish Power and Germany’s rail system. The Russian Federation has been particularly hard hit.
Whats Happening
Ransomware such as this encrypts your files and demands payment to unlock them again – the ransom. In most cases this cannot be fixed by a third party (eg your IT support). Your machine is recoverable but your files aren’t.
For most private individuals the biggest worry would be having all your personal files encrypted, not the risk of spreading the worm around a network. That is more of a problem for corporates, and the threat applies to all versions of Windows including 10.
It is reported the primary vulnerability (to spreading the worm) is Windows XP, but Vista, Server 2003, Server 2008 and Windows 8 are vulnerable. Maybe Windows 7 too, but currently no special patch has been released. Be aware that Windows 10 would also have been vulnerable if not for an automatic update last month; much of this episode is about Microsoft’s purely commercial policy on (not) supplying (free) updates to older operating systems.
This patch DOES NOT protect your files in any way
The worm spreads from infected machines via a weakness in in a legacy file sharing protocol SMB v1; as a quick protection, this can be disabled. If you do not use file sharing then only your machine is affected.
The world has rather been taken by storm, its the weekend and initial firefighting techniques involve shutting down all vulnerable systems. Consequently there hasn’t been so much reported about the how and why. Updates to follow no doubt.
Updates
A techie at Telefónica confirmed that the initial infection vector was a phishing email.
Many assumed Wannacry could infect any pre-Windows 10 systems, however it mostly infected Windows 7 computers that hadn’t pick up Microsoft’s March security patch for the SMB bug. That’s because the malware’s implementation of EternalBlue is ineffective on Windows XP and Windows Server 2003: it simply wouldn’t work reliably. In other words, contrary to popular belief, the outbreak didn’t hit very many WinXP and similarly aging boxes at all – it was mostly unpatched Win7 and Server 2008 machines in enterprises and other large organizations that were slow to apply Microsoft’s fix
Its also being reported a number of Windows boxes have been connected (by their owners) directly to the Internet and have their file sharing SMB services exposed to all and sundry. No real wonder they have been infected then! Anyone competent could have told them this was a bad idea ever since 1997. Catch up please.
Even if you dont have a Twitter account, you can keep an eye on my updates at twitter.com/nw3biz
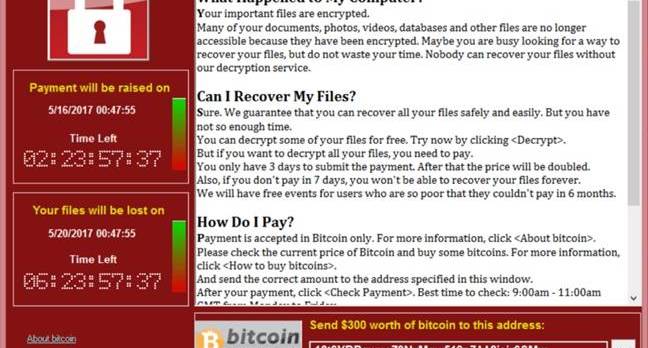
Unfortunately, unless you store your backups (if you have any) offline, all network accessible files are vulnerable to attack. For home users, a simple backup onto a USB stick or external drive can be invaluable.
Protection: What’s the Risk?
Although more sophisticated in appearance and delivery, there are similarities to the out break of the Locky virus (and variants) from last year. This ransom -ware is becoming big business, pay up or loose access to your files forever.
It seems the worm is most likely spread as an email attachment, although possibly via special web pages. Email attachments are the most likely vector, in this case and most others. Unfortunately anti-virus AV software is somewhat limited in the case of ‘zero-day attacks’. Normally AV companies release updates to counter these threats, but only the day after – hence new, unknown attacks are on ‘zero day’. You can never be fully protected.
It cant be emphasised enough: dont open attachments that you do not expect. In fact, dont even open the email, send to spam it immediately. Never mind that you actually have an uncle in Nigeria or are desperate for the latest diet pill, remember someone is looking to make you their next target. You and 100 million others just received that email. Some will fall victim, dont let it be you.
Just like any locked door, the weakness is the person opening it
If you have any network data stores or servers, it might be worth considering leaving them switched off for a while until everything is patched and updated. Ditching Microsoft email clients, Outlook, Mail etc. might be a good idea too.
How about a regular backup routine? If you don’t have much days to site this could be kept very simple.
Remember, this isn’t over and such attacks are becoming more common. Ransomeware is good income for criminal and terrorist groups as everyone has something on their computer that is valuable to them.
Infected?
Although Microsoft patched this vulnerability for current operating system in March, older systems do not update automatically. MS have, unusually, made a patch available Microsoft Security Bulletin MS17-010 – Critical and are providing more information at this page Customer Guidance for WannaCrypt attacks
These proceedures will help prevent the worm moving around your network, affecting your colleges or family’s computers.
What if you’re files/documents have already been encrypted? Sadly there is currently no known way of reversing the damage.
